WE BUILD CYBER SECURITY SOLUTIONS
We desing, implements, and maintains systems and procedures that permit for your business to utilize technology productively
While maintaining the confidentiality, integrity, and availability
A few things we’re great at
A virtual Chief Information Security Officer (vCISO) is a security professional who works on behalf of organizations to help them manage their information security program.
While a CISO is typically a full-time employee, often a member of the c-suite, a vCISO is an individual or team that brings their expertise and experience to the table on-demand as a contractor.
Determines how ready you are to prevent and defend against a ransomware attack.
We will help your organization identify your most critical business services and assess your business’s ability to quickly detect an attack, contain the damage to your critical systems, and highlight where to focus resources regarding backup/restore capabilities.
With Digetech Ransomware Readiness Assessment, we help mitigate risk by preparing organizations on how to prioritize efforts to reduce risk in the shortest time possible.
With the risk assessment, our risk management consultant identifies your organization’s security vulnerabilities, inefficiencies, and noncompliance with standards for security policies that are of low-, medium-, and high-risk.
Risk Assessment Services identify the strengths and weaknesses of your organization to develop new security plans and policies.
Risk Management Services & Risk Assessment Services justify spending and help your organization make smarter purchases in the long-term to prevent overspending because of potential security and financial exploitations.
Your organization’s cyber risk extends beyond your organization. Anyone you work with —
anyone who has access to your organization’s data — has the potential to open your business up to more vulnerabilities.
With Third-Party Risk Management Services, we help effectively respond to Third-Party Risk Assessment questionnaires and conduct Third-Party Risk Assessments of your vendors, ensuring that critical data is secure
As part of these services, we:
Review and assess your existing incident response documentation.
Interview key employees and executives to gather additional information and perspectives on incident response planning, organizational roles, and responsibilities.
Review recent incidents to understand current processes and technologies in place to support a security incident investigation.
Digetech evaluates your organization’s cyber crisis processes to Detect, Respond, Investigate, and provide incident response awareness.
Our team will setup a Tabletop Exercise and guides your team through a targeted attack scenario that accurately and effectively mimics the experience of a targeted attack
Psychological manipulation is a tactic commonly used by cybercriminals. By crafting emails and web pages that imitate those of known organizations and contacts, fraudsters aim to trick individuals into clicking dangerous links, opening malicious attachments, and disclosing personal details.
Digetech’s social engineering services allow you to accurately assess the ability of your systems and personnel to detect and respond to email phishing attacks. Gain precise insight into the potential risks through customized assessments created for your organization.
Every organization has some form of written policies and operating procedures. Often these policies are not kept current with new practices and new laws.
Digetech can focus on upgrading and rewriting both standard policies but also assist with indigenous procedures, bringing the Policy & Procedures manual up to date.
Policies and procedures are living documents that should grow and adapt with a company.
Comprehensive threat and Vulnerability Assessment is essential to securing your organization.
Is a comprehensive evaluation of a system for exposed vulnerabilities without their direct exploitation.
Digetech helps clients to challenge assumptions about their network security. Our experts combine years of practical hand-on experience to test the way adversaries hack.
They perform thousands of engagements per year, leveraging a goal-based approach and real-world threat intelligence to provide actionable findings that matter.
Our Digital Forensics Investigator’s first step is to clearly determine the purpose and objective of the investigation in a free consultation.
We will work with you to identify where your data is located. We will document the legal chain of custody of the media, and we will make a bit-by-bit copy and preserve the original.
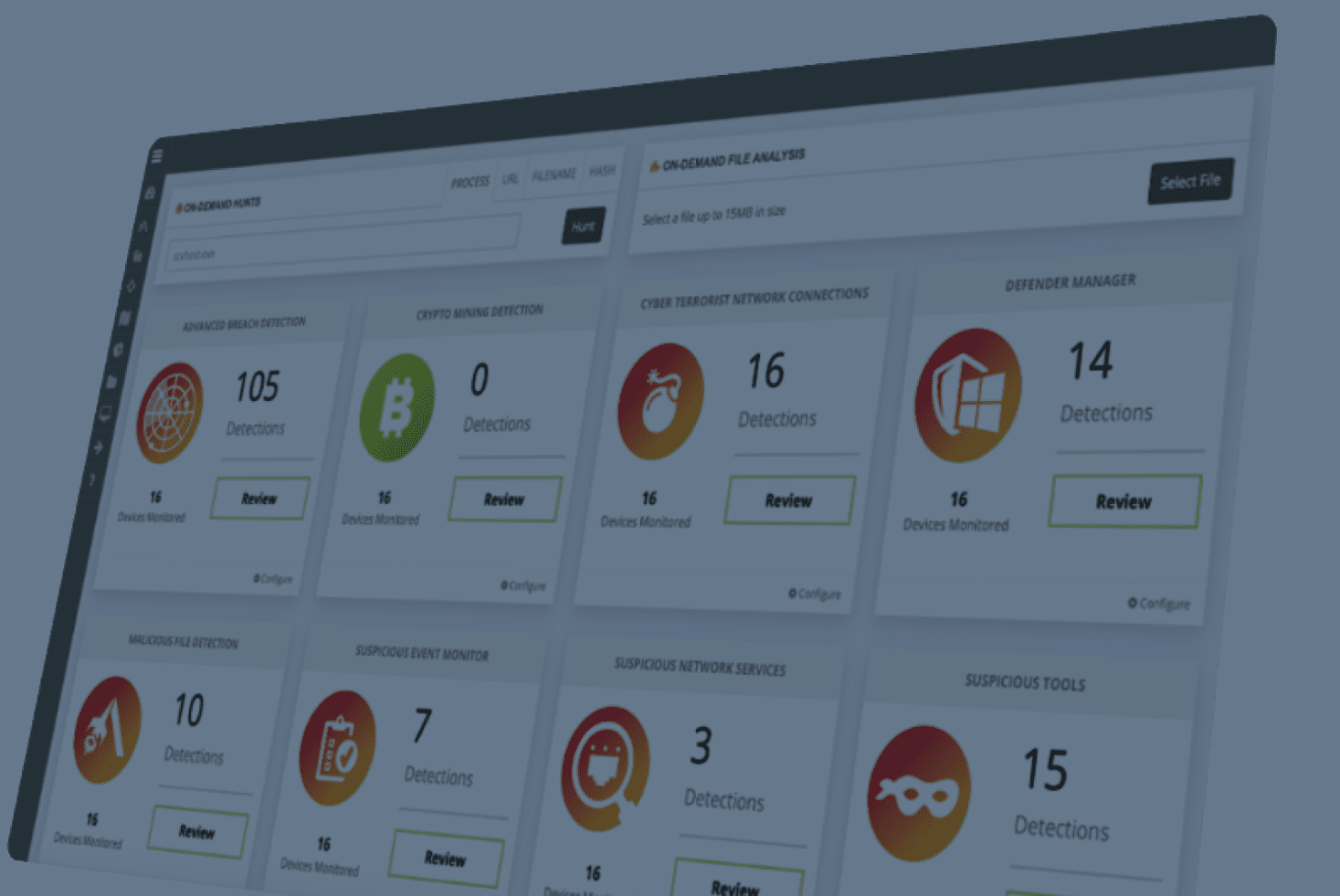
Stop attackers in their tracks with our managed cybersecurity detection and response solution backed by a world-class security operations center.
The managed SOC team will analyze the network environment and technologies to properly place and configure network threat sensors, log collectors, and scanners.
Digetech Cyber Insurance Readiness Service includes all the assessments to help your organization understand if your cybersecurity program can meet these changing insurance coverage requirements.
Digetech can help set your organization up for success when obtaining cyber insurance coverage, or to reduce the cost of cyber insurance premiums.